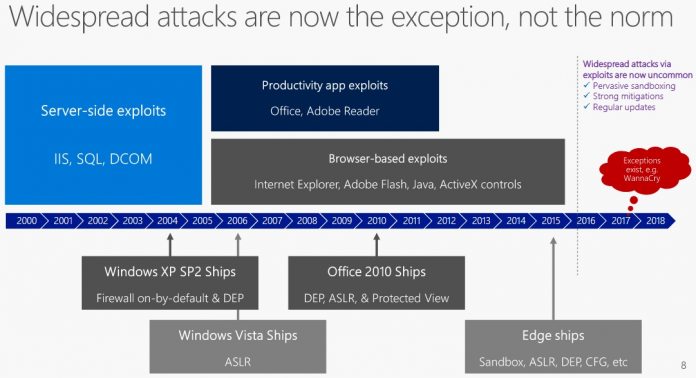
Matt Miller, a Microsoft security engineer, told attendees the company has shored up its products and widescale attacks through security flaws are rare. Miller says Microsoft’s ongoing improvement of security features has helped protect customers. Among those features are on-by-default firewalls, Protected View in Office, Address Space Layout Randomization (ASLR), and app sandboxing. Essentially, low-level cyberattacks are now finding it nearly impossible to rupture Microsoft’s security blanket. As for more sophisticated attacks, those attacks are finding it much more difficult. Miller admits scaled mass attacks do eventually happen, but typically once Microsoft has issued a fix.
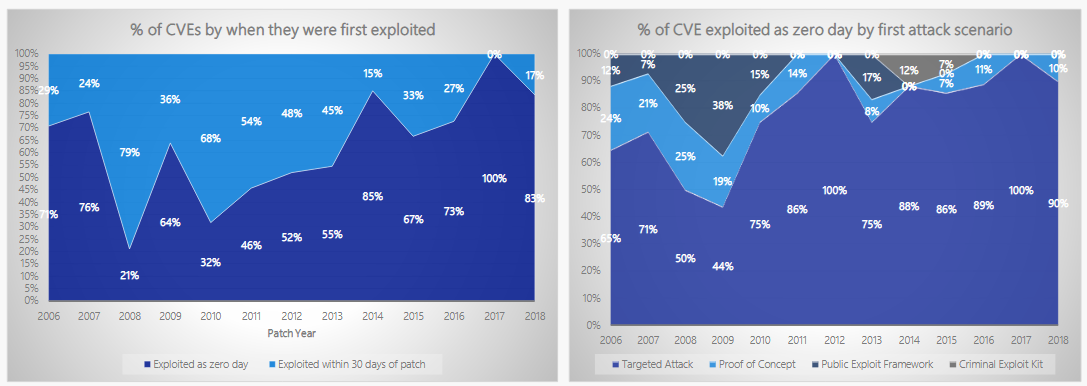
Miller points to data in 2018 that shows 90% of all zero-day attacks on Microsoft services were targeted attacks. In other words, these were no flaws sent out by spam attacks but were more organized such as from state-sponsored bad actors. “It is now uncommon to see a non-zero-day exploit released within 30 days of a patch being available,” Miller also added. While attacks on zero-day and non-zero-day flaws do happen, it is almost always long after a fix has been issued. Miller says this is because Microsoft services are increasingly blocking out attacks, requiring more sophisticated exploit methods.
Less Power to Attackers
To emphasize the improved security climate at Microsoft, Miller showed two charts. On the left (above), he showed Microsoft’s increased security efforts in recent years. This highlights how proactive the company has been in sending out fixes with a CVE identifier. On the right, the chart shows know flaws in Microsoft products increase, less of these vulnerabilities are morphing to full attack methods for hackers. Two charts in Miller’s presentation perfectly illustrate this new state of affairs. The chart on the left shows how Microsoft’s efforts into patching security flaws have intensified in recent years, with more and more security bugs receiving fixes (and a CVE identifier).